Notice: Trying to access array offset on value of type null in /srv/pobeda.altspu.ru/wp-content/plugins/wp-recall/functions/frontend.php on line 698
 How much can be lost? Multiply the proportion of the loss by the dollar worth of the asset to get a monetary quantity for that risk. Then transfer on to the next danger in your checklist. It doesn’t nonetheless, answer all the questions related to risk — like what happens to productivity if there’s a cyber attack? That’s where qualitative risk assessment is available in. A qualitative risk assessment is much less about numbers and extra about what would really happen, day-to-day if one of the risks in your record had been to happen. While a quantitative risk assessment is easy and numbers-based mostly, a qualitative security risk assessment methodology is carried out by talking to members of various departments or models and asking them questions about how their operations would be impacted by an attack or a breach. Specifically, you would possibly ask how a team’s productiveness could be affected if they couldn’t access specific platforms, functions, or data. These interviews will present an assessor which programs and platforms are mission-vital for particular groups, and which aren’t.
How much can be lost? Multiply the proportion of the loss by the dollar worth of the asset to get a monetary quantity for that risk. Then transfer on to the next danger in your checklist. It doesn’t nonetheless, answer all the questions related to risk — like what happens to productivity if there’s a cyber attack? That’s where qualitative risk assessment is available in. A qualitative risk assessment is much less about numbers and extra about what would really happen, day-to-day if one of the risks in your record had been to happen. While a quantitative risk assessment is easy and numbers-based mostly, a qualitative security risk assessment methodology is carried out by talking to members of various departments or models and asking them questions about how their operations would be impacted by an attack or a breach. Specifically, you would possibly ask how a team’s productiveness could be affected if they couldn’t access specific platforms, functions, or data. These interviews will present an assessor which programs and platforms are mission-vital for particular groups, and which aren’t.
 Organizations conduct risk assessments in lots of areas of their companies — from safety to finance. Cybersecurity danger assessments deal exclusively with digital assets and knowledge. There are two important types of risk assessment methodologies: quantitative and qualitative. Quantitative danger assessments concentrate on the numbers — to perform a quantitative risk assessment a staff uses measurable data factors to assess risk and quantify it. To perform a quantitative risk assessment, your group will start by compiling two lists: a listing of potential risks and an inventory of your most necessary digital property. The second checklist might embody items resembling helpful information, your IT infrastructure and different key property. Once you’ve made your checklist of property, you’ll assign a dollar value to each merchandise — this can be tough for line gadgets resembling buyer data or other priceless info for which there is no such thing as a set financial worth. Then have a look at your checklist of risks. Which asset can be affected by the danger at the top of your listing?
Organizations conduct risk assessments in lots of areas of their companies — from safety to finance. Cybersecurity danger assessments deal exclusively with digital assets and knowledge. There are two important types of risk assessment methodologies: quantitative and qualitative. Quantitative danger assessments concentrate on the numbers — to perform a quantitative risk assessment a staff uses measurable data factors to assess risk and quantify it. To perform a quantitative risk assessment, your group will start by compiling two lists: a listing of potential risks and an inventory of your most necessary digital property. The second checklist might embody items resembling helpful information, your IT infrastructure and different key property. Once you’ve made your checklist of property, you’ll assign a dollar value to each merchandise — this can be tough for line gadgets resembling buyer data or other priceless info for which there is no such thing as a set financial worth. Then have a look at your checklist of risks. Which asset can be affected by the danger at the top of your listing?
You may also ask buyer-going through groups how a breach will have an effect on service supply or those that manage vendors about how an attack will interfere with provide strains. Qualitative risk assessments aren’t as exact as quantitative assessments are, but they provide an vital piece of data — an assault is about greater than its monetary ramifications. It can even throw business operations into chaos. If you already know forward of time how danger may impact each team’s productiveness, you may have again-ups in place to mitigate those dangers. When you’re creating your company’s data security administration program, it’s essential to understand that you’ll need to include methodologies when you’re assessing threat. Your leadership have to be ready for the financial effects of a breach as well because the impact an attack might have on enterprise operations. By identifying danger and realizing how it will influence your online business, you’ll be better prepared to mitigate the impact of a risk ought to it happen. SecurityScorecard can enable you to see your risks by monitoring the cyberhealth of your enterprise across 10 teams of danger factors with our simple-to-perceive security rankings. By constantly monitoring your enterprise’s safety, you’ll be able to take action and protect your knowledge and that of your prospects and companions.
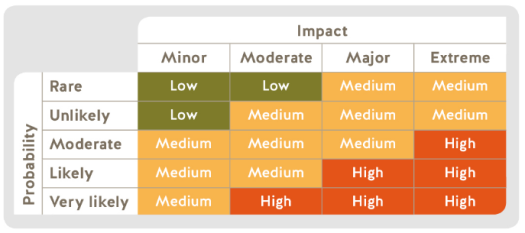
Every company handles sensitive data — buyer knowledge, proprietary information, info property, and employees’ personal information — all of those information come with risk hooked up to them. How can your group perceive exactly how a lot threat you face with regards to the knowledge you’re storing and your cybersecurity controls? How are you able to prepare for that threat before a breach occurs? Cybersecurity risk assessments are a significant a part of any company’s info safety administration program — they make it easier to understand which security dangers your vital belongings face, how it is best to protect these property, and the way much you need to finances to protect them. What is risk assessment? Risk assessment is, broadly, the means of figuring out and analyzing potential future occasions which will negatively impact your group, how seemingly each kind of threat is, and the way a lot of an influence a danger might have on your online business. A risk assessment may show you how to resolve how a lot of every kind of threat your group is able to tolerate.
Design a plan: Failure to plan implies that dangers on the job will proceed to pose a threat to your company, individuals, and property. This plan must be detailed and easy to implement, with clear communication flowing right down to those liable for implementation. Allocate needed sources: What resources are required to ensure the danger controls are in place? Resources might include time, money, tools, or supplies that provide safety to everybody concerned. Accountability for implementation: Finally, how will you hold managers and workers accountable for following the designated plan? Good intentions won’t keep the program going. You have to be clear in your expectations and communicate the follow-up accountability examine-ins to guage the team’s progress. Monitoring and changes: Ongoing monitoring is needed to determine whether you efficiently eradicated the hazard. If the risk can’t be removed, then this monitoring ensures that the risk is controlled appropriately. Implement a consistent schedule for follow-ups so that nothing is ignored sooner or later.
